Crypto Chaos: Hackers Hijack 18 Code Packages in Brazen Digital Heist
Major Security Breach: 18 Popular JavaScript Packages Compromised in Sophisticated Phishing Attack
In a stunning cybersecurity incident, more than 18 widely-used JavaScript code packages—collectively downloaded over two billion times each week—were temporarily infiltrated by malicious software after a critical vulnerability emerged through a targeted phishing scheme.
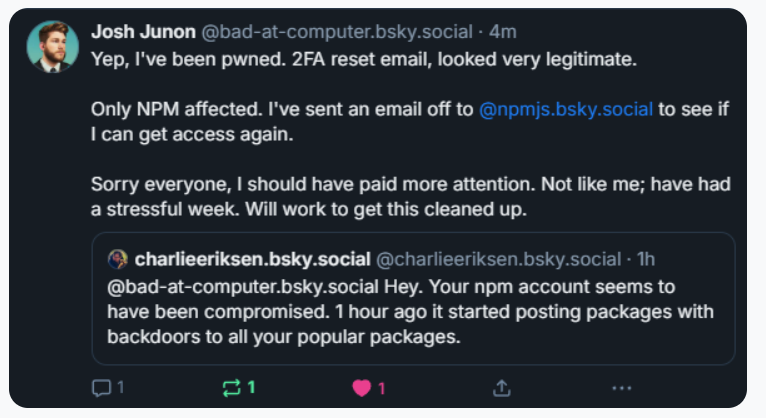
The attack targeted a key developer involved in maintaining these essential open-source projects, exploiting human vulnerabilities to gain unauthorized access. This breach highlights the increasing sophistication of cybercriminals who are constantly seeking to exploit potential weaknesses in the software development ecosystem.
While the initial details suggest a brief compromise, the incident underscores the critical importance of robust security practices and vigilance within the developer community. Cybersecurity experts are currently investigating the full extent of the potential damage and working to mitigate any lingering risks.
Developers and organizations using these packages are advised to stay informed and apply any recommended security updates as they become available.